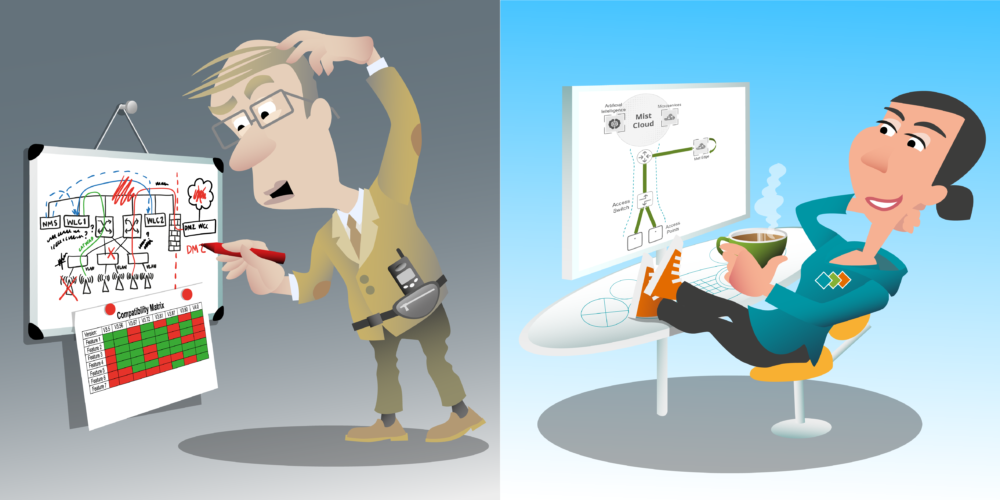
Hello. In this video we’re going to talk about wireless LAN architecture. Now architecture for traditional wireless LAN systems can start to get very complicated and messy very quickly, especially when you have multiple wireless LAN controllers managing your access points. Then you have a wireless network management system managing the controllers. Let’s take poor Stanley here, he’s trying to find a correct architecture of his wireless LAN solution, and he has controllers in his core, but he also has DNZ controllers and he’s trying to work out which wireless LANs should be used in distributed forwarding and which ones should be used in centralized forwarding. Does he need redundancy in the management plane for the wireless network management system? What happens if an access point can’t reach a controller?
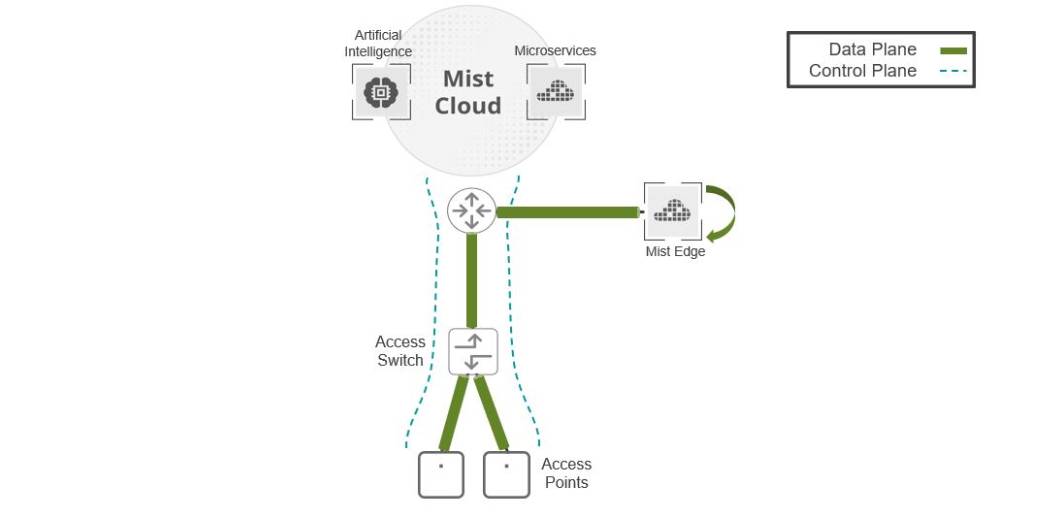
He also has his compatibility matrix trying so he can work out which features and architectures are supported by different code versions. To be honest, his head is just spinning. Well, thankfully, when designing a Mist wireless LAN system, the architecture is simple. Let’s take a look at a basic Mist architecture. You see, Mist is a cloud managed wireless LAN systems. All APs are managed and controlled by the Mist Cloud. Simple. While management and control traffic flow to and from the cloud, all data traffic is capped local. Therefore, the access points need to be able to forward all user traffic directly to the destination, which means that all user VLANs need to be trunked to each access point.
Now, for many customers, this simple, scalable and robust architecture is all that’s needed. However, there are a few use cases where this is not the case. There’s a few times when it’s not possible to trunk all VLANs to all APs. In these cases we have a Mist Edge appliance, which can be deployed. Now, Mist Edge appliances terminate data tunnels from APs. I want to be clear, a Mist Edge appliance is not a controller. All access points and the Mist Edge appliance itself are managed and controlled by the Mist Cloud. The Mist Edge is primely there just to terminate data tunnels.
Let’s look at some common Mist Edge use cases. The first of them comes when replacing traditional controller base wireless LAN solutions where all the traffic was tunneled back to the wireless LAN controller. Now, you might find in these situations that the wired architecture is not set up for trunking all wifi user VLANs to each AP, and it would need a significant investment to re-architecture the wired infrastructure to enable that to be possible. In these scenarios, we can simply place a Mist Edge appliance in the place of the wireless LAN controller to terminate old data tunnels.
Now, another use case for a Mist Edge would be terminating guest traffic in a DMZ. It might be that while all corporate user VLANs will be trunked to each access point, the guest traffic needs to be tunneled back to the DMZ. Local councils in the UK, for example, are not allowed to have any publicly accessible VLANs trunked over their corporate infrastructure. Therefore, the only way to provide guest access is to tunnel the guest traffic back to a Mist Edge in the DMZ.
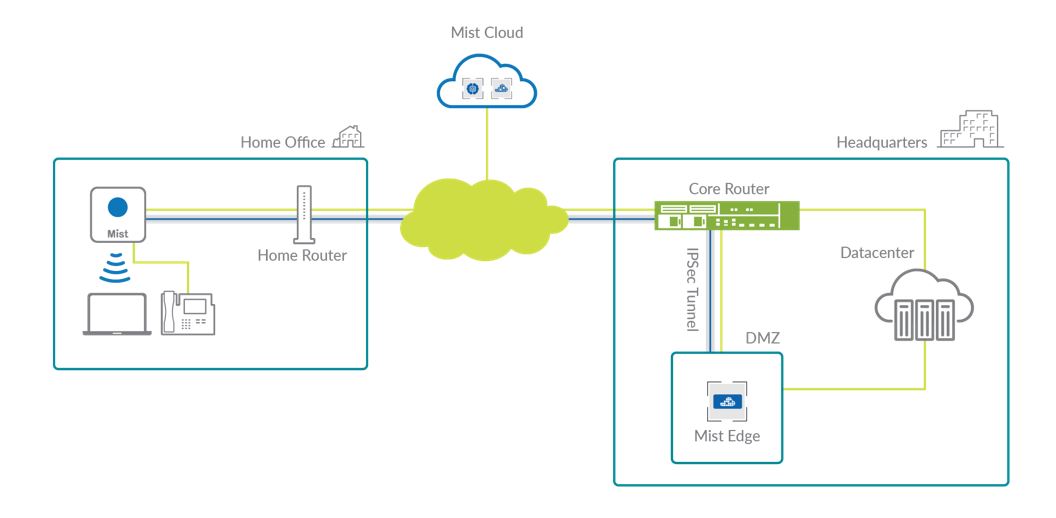
The final use case I’d like to discuss with you is where we are going to extend the enterprise wireless LAN for remote workers. In this scenario, a Mist access point can be given to the remote worker and the access point will establish an IPSec tunnel back to a Mist Edge in the corporate headquarters. Data traffic can then be tunneled back to the corporate headquarters providing the user with the same access to all the same services they do when at the headquarters.
Let’s take a look at the different Mist Edge models. The ME-X1 is the smallest appliance and can support up to 500 access points and 5,000 clients with a maximum throughput of two gigabits per second. Now this is aimed at smaller scale deployments and the ME-X1 also only has a single cabled power supply, so it’s not suitable for environments where redundant power supplies are required.
Now next we have the ME-X5, and the ME-X5-M. Both of these models support 5,000 access points and up to 50,000 clients, and they both support hot-plug redundant power supplies. Now the main difference between these two models is a maximum throughput with the ME-X5 supporting up to 20 gigabits of throughput and the ME-X5-M supporting up to 40 gigabits.
Now for large sort of campus environments where you need to support a very large number of access points and clients, we have the ME-X10, which can support up to 10,000 access points and a hundred thousand clients missed. Mist also have a VM Mist Edge, the ME-VM, which can support up to 500 access points and 5,000 clients, although you can cluster VMs together to support up to a thousand access points.
Now data forwarding is configured per wireless LAN and when configuring a wireless LAN, we can choose where we want the data to be forwarded to. It could either be forwarded through ethernet zero, which is a default or ethernet one. In these two scenarios, we need to make sure that the VLAN for that wireless LAN is trunked to the ethernet [inaudible 00:06:48] of the access point, or we can choose to tunnel it back to a Mist Edge. There’s also an option to tunnel traffic back to any device which can terminate an L2TP tunnel, such as a Juniper SRX gateway. Now its simple approach to wireless LAN architecture means that while Stanley continues to [inaudible 00:07:15] over his wireless LAN architecture, Misty can put her feet up satisfied and enjoy a nice cup of tea. Thank you for watching. Goodbye.
Mist Architecture Options
1. Local AP bridging
In this architecture all user VLANs are tunneled to each AP

2. Traffic tunneled to Mist Edge
WLAN traffic is tunnel to a Mist Edge. This solution is ideal when replacing a traditional controller-based architectures and it is not possible to trunk all the user VLANs to each AP. A mist edge may be place in the DMZ to provide guest users with access to an external internet connect.
3. Extending the Enterprise (Work from Home)
This solution enables you to securely extend your corporate SSID and AAA services to remote and home offices, with and an IPSec tunnel between your AP and the Mist edge
Next Videos